Permission Policies
In Spot, a permission policy is a set of one or more permissions. When a policy is attached to a user or a group of users, the policy grants its permissions to those users. A permission policy can apply to one or more individual Spot accounts, or a policy can apply to an entire Spot organization.
A permission allows a user access to a Spot service (such as Ocean or Elastigroup) and specifies which actions a user can take.
Default Permission Policies
Spot comes with a number of default policies. You can use these out of the box and create new policies that are specific to your organization.
- Account-level permissions:
- Account Editor
- Account Viewer
- Elastigroup Full Access
- Ocean Full Access
- Organization-level permissions:
- Credit Card Editor
- Cloud Analyzer Editor
- Organization and account-level permissions:
- Admin
Custom Policy Conditions
Custom policy conditions give you more control of your Spot resources at the organization and account level:
- Condition operators that contain the condition keys:
- Resource retrieval
- Resource attribute
- Condition values (attribute value) that should match keys and values received for the given resource in the request.
You can allow or deny access to a specific resource if the condition in the policy matches the requested data (such as resource name, resource inner configuration).
This is supported for AWS and Azure users.
Policy Rules
These rules apply to policies:
- An action that is not explicitly allowed by a policy is denied by default.
- A policy-based user with no policies is equivalent to a viewer user. Organization administrators, account editors, and policy-based users with the proper permissions are able to grant permissions.
- All API tokens that belong to you are affected by your current policy.
- Permissions to create objects (such as elastigroup:create*) do not grant permissions on the created objects themselves.
Create a Permission Policy
-
In the Spot console, click the user icon
> Settings.
-
Click Organization > Permission Policies > Create New Policy.
-
Enter a Policy Name (and Policy Description).
noteNames cannot include these characters:
+ = @ -
Select the type of Permission Management:
- Account Permissions: These permissions are for products and services that have resources at the account level. You select the relevant accounts separately for each user or group once you attach the policy to them.
- Organization Permissions: These permissions are for products and services that have resources at the organization level.
noteKeep in mind that once a policy has been created, you cannot change the policy type.
-
Click Continue.
-
Select the Service and Effect:
- Allow means that actions marked are allowed. Any unmarked items are not allowed. This is the default behavior for defining a service.
- Deny means that actions marked are denied. Any unmarked items will not be denied.
-
Select the Actions for the Service. If you do not want to allow all the high-level actions included in the standard set of actions, remove the selection from the high-level action and select only the specific actions.
Example of create actions for the Elastigroup service
Since the Delete action is unmarked, this policy will not allow users to delete anything in Elastigroup.

Edit the JSON�
-
In a permission policy, click JSON.
-
Turn on Edit Mode.
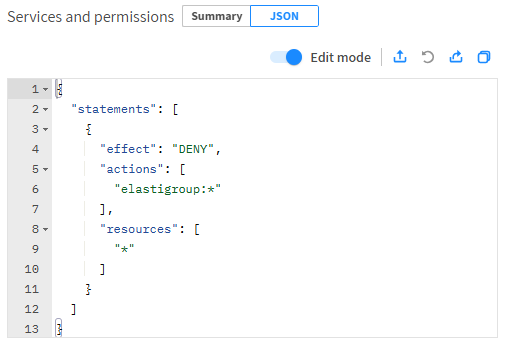
Statements
A statement includes:
-
Effect allows or denies actions. Values are ALLOW or DENY.
-
Actions is an array of actions formatted as
[serviceName]:[actionName]. You can use wildcards (*) in the[serviceName]and[actionName]:- elastigroup:update
- ocean:roll
- elastigroup:describe* allows all Describe actions, such as -elastigroup:describeDeployments, elastigroup:describeGroup
- elastigroup:* will allow all Elastigroup actions.
-
Resources is an array of resources formatted as
[serviceName]:[resourceId]. A resource represents a Spot resource, such as an Ocean cluster or an Elastigroup. The effect and actions are applied to the resource. You can use wildcards (*) in the[serviceName]and[resourceId]:- All resources:
* - All Elastigroup resources:
elastigroup:* - All groups starting with sig-214:
sig-214*
- All resources:
Policy Conditions
Custom policy conditions let you create conditions within policies for granular control. Supported resources include Spot managed AWS and Azure resources.
Conditions include:
-
Logical operator (optional) defines the logic between the value-based operators. Using a logical operator requires at least two value-based operators.
-
Value-based operator:
- StringEquals compares two strings and returns true if equals, otherwise returns false.
- StringNotEquals compares two strings and returns false if equals, otherwise returns true.
- StringContains compares two strings and returns true if the first string contains the second, otherwise returns false.
- StringEqualsIgnoreCase compares two strings and returns true if the strings are the same length, and corresponding characters in the two strings are equal ignoring case.
- StringPatternMatch compares two strings and returns true if the string matches the given regular expression.
If the condition contains more than one condition operator, AND is used between them. This means that all the operators should return true.
-
Resource retrieval supports AWS and Azure resources.
This part is responsible for the definition of which resource should be tested with the condition operator. It consists of a Spot prefix (
spot) and resource name (such aselastigroup,ocean), separated by a colon:. -
Resource attribute is an optional name, tags, or resource attribute. Examples for a full resource retrieval definition:
- "spot:ocean:name"
- "spot:elastigroup:tags/Email"
-
Attribute value is a single string, single variable (such as
${spot:userEmail}), or array of values. You can have multiple attribute values for the same field. For example,"spot:elastigroup:name": ["elastigroup-1","elastigroup-2"]and OR is used between them.
Example 1: Update Elastigroup resource
This policy lets users with example@mail.com email address update the Elastigroup resource:
{
"group": {
"name": "eg-example",
"compute": {
"launchSpecification": {
"tags": [
{
"tagKey": "DeveloperEmail",
"tagValue": "example@mail.com"
}
]
}
}
}
}
This policy checks for the DeveloperEmail tag, and lets users with this email address perform the update Elastigroup action.
{
"statements": [
{
"effect": "ALLOW",
"actions": [
"elastigroup:updateGroup"
],
"resources": [
"*"
],
"condition": {
"StringEquals": {
"spot:elastigroup:tags/DeveloperEmail": "${spot:userEmail}"
}
}
}
]
}
Example 2: Resource name contains
This policy enables performing Ocean-related operations on clusters with names containing ocean-example-1 or ocean-example-2.
{
"statements": [
{
"effect": "ALLOW",
"actions": [
"ocean:*"
],
"resources": [
"*"
],
"condition": {
"StringEqualsIgnoreCase": {
"spot:ocean:name": ["ocean-example-1", "ocean-example-2"]
}
}
}
]
}